Some links though:
Firstly, from Microsoft itself:
A security feature bypass vulnerability exists in Windows 10 Mobile when Cortana allows a user to access files and folders through the locked screen. An attacker who successfully exploited this vulnerability could access the photo library of an affected phone and modify or delete photos without authenticating to the system.
To exploit the vulnerability, an attacker would require physical access and the phone would need to have Cortana assistance allowed from the lock screen.
So I think 'access files and folders' is a bit misleading. Perhaps if you kept super-secret or compromising photos on your phone then you'd be a tiny bit worried. But which of us does that without some extra form of protection?
Still, you'll now be wondering how hard it is to execute the vulnerability? It's VERY hard - I tried numerous times on my IDOL 4 Pro and I wasn't fast enough. So I'll have to take Reddit's word for it:
Reproducible steps:
On a locked device, open the Camera and take a picture.
Preview the picture using the Preview thumbnail. It is recommended to wait until the Camera finishes to add “final touches” to the picture.
Open Cortana.
Press the Back button twice to return to the Lock screen. The screen should now be black.
Close and open the screen using the power button of the device.
Open Cortana again. Before Cortana launches, the Camera application will appear for a short time. In that tiny time frame, press the Preview thumbnail. If missed, repeat all stages.
The new picture should open (Cortana might still be talking in the background), and the “View all photos” button should work like in unlocked mode.
The disclosers also say:
We reported this issue to Microsoft in December 2018, a year before the operating system's end-of-life. After nine months of evaluations and analysis, they decided not to patch the vulnerability because of the “limited users of Windows 10 Mobile, the physical access requirement to reproduce this issue, and the difficulty in steps to reproduce.”
Even though it's very hard to do in reality, there's video proof:
So there we go - it's a minor flaw and, given an OS still under active development, it would get addressed just to be on the safe side. But given that all work on the Windows 10 Mobile interface code* had already stopped by the time the issue was disclosed, and given the obscure nature, I'm not at all surprised that Microsoft chose not to do anything, risking breaking something else in what had become a fairly stable UI in the process.
* as opposed to that on the kernel and core components, which continue to get security tweaks to this day (and until the end of 2019)
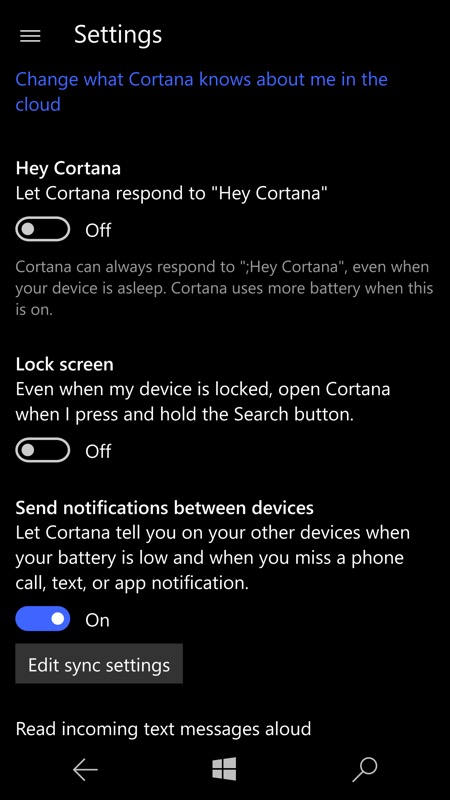
If you're still worried (you shouldn't be) then you can always disable lock screen Cortana access, as shown above...
