Anyway, from ZDNet:
Speaking at the RSA security conference last week, Microsoft engineers said that 99.9% of the compromised accounts they track every month don't use multi-factor authentication, a solution that stops most automated account attacks. The cloud giant said it tracks more than 30 billion login events per day and more than one billion monthly active users. Microsoft said that, on average, around 0.5% of all accounts get compromised each month, a number that in January 2020 was about 1.2 million.
While all account hacks are bad, they are worse when the account is for enterprise use. Of these highly-sensitive accounts, only 11% had a multi-factor authentication (MFA) solution enabled, as of January 2020, Microsoft said.
In most cases, the account hacks happen after rather simplistic attacks. The primary sources of most hacks of Microsoft accounts was password spraying, a technique during which an attacker picks a common and easy-to-guess password, and goes through a long list of usernames until they get a hit and can access an account using said password.
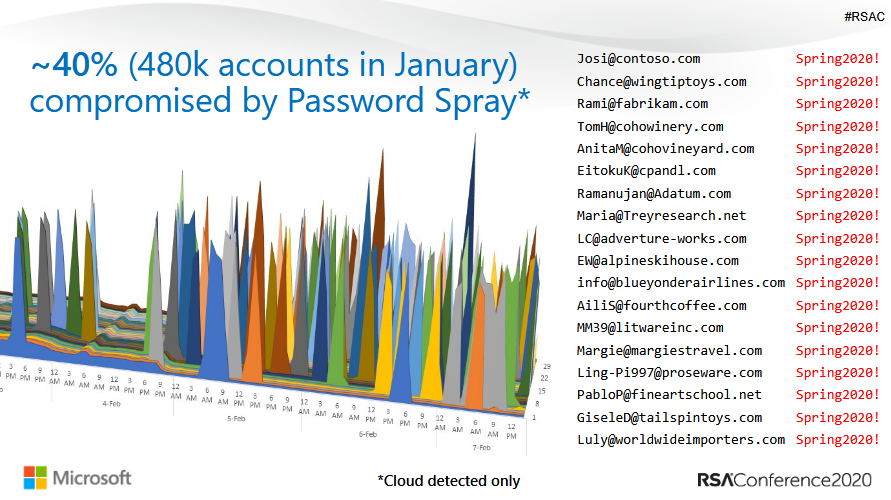
The second source of account hacks, Microsoft said, was password replays, a technique that involves an attacker taking credentials leaked at another company and then trying the same credentials on a Microsoft account, hoping the user reused usernames and passwords.
I'll bet that most AAWP readers are tech-savvy enough (by now) to have implemented multi-factor authentication on all important accounts in their lives. But the RSA keynote is still a sobering reminder.
